Introduction
OSPFv3 authentication is quite generally quite straightforward to configure between two Cisco devices. There are some great posts regarding this topic, in fact one of the best I’ve read is by the great Jeremy Stretch.
http://packetlife.net/blog/2008/sep/3/ospfv3-authentication/
The issue I came across was how lacking in information there was to authenticate between vendors.
Configuration
The configuration on the Cisco side is simple as Stretch details in his post. You can either enable auth per interface or for the area.
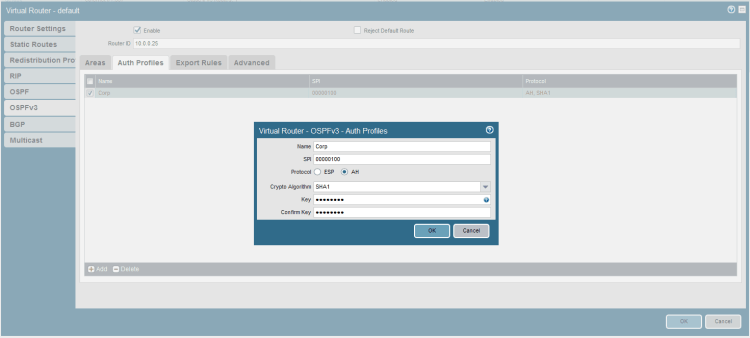
The spi is an arbitrary value however it must match between peers. In Cisco configuration the value is added as an integer but the value must be added in hex format on the Palo Alto so some translation is in order. The SHA1 hash on the Cisco side needs no formatting but on the Palo Alto it must be formatted correctly otherwise you will get a commit error with the following details:
error: failed to parse IPsec manual-key
Example
Cisco configuration:
R1(config-rtr)# area 0 authentication ipsec spi 256 sha1 0 d69ac67f6c8b6ff82ab115c1571c48b182f563b6
Palo Alto:
Notice the SPI is not 256 but 00000100, that is because the decimal value 256 is 100 written as a hexadecimal value. The following explains the maths much better than I could:
https://www.binaryhexconverter.com/decimal-to-hex-converter
The key format is also important, you must format your key in the following way:
xxxxxxxx-xxxxxxxx-xxxxxxxx-xxxxxxxx-xxxxxxxx
For example:
d69ac67f-6c8b6ff8-2ab115c1-571c48b1-82f563b6
Hope this can save some time when you configure OSPFv3 authentication on your hardware.



Thank you! I guess it helps to pay attention to the contextual help.
No problem Nathan. Had me stumped for a while.
Thanks for those hints, man. I was lost with the same problem!